Quick Info
Media
Description
HCL AppScan on Cloud (ASoC) is a SaaS solution for all application security testing needs. It consolidates all HCL security testing capabilities into a single service that provides a uniform experience for all technologies. HCL Security ASoC can scan web, mobile, and desktop applications using dynamic and static techniques.Quick Info
ucv-ext-asoc:3.0.19.tar
Uploaded: 10-Mar-2023 14:34
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:3.0.19Release Notes
ucv-ext-asoc:3.0.16.tar
Uploaded: 15-Dec-2022 14:08
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:3.0.16Release Notes
ucv-ext-asoc:3.0.12.tar
Uploaded: 13-Sep-2022 06:17
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:3.0.12Release Notes
ucv-ext-asoc:3.0.11.tar
Uploaded: 07-Jul-2022 04:37
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:3.0.11Release Notes
ucv-ext-asoc:3.0.9.tar
Uploaded: 24-May-2022 05:47
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:3.0.9Release Notes
ucv-ext-asoc:3.0.5.tar
Uploaded: 28-Jan-2022 16:57
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:3.0.5Release Notes
ucv-ext-asoc:3.0.1.tar
Uploaded: 25-Aug-2021 08:38
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:3.0.1Release Notes
ucv-ext-asoc:2.0.1.tar
Uploaded: 03-Aug-2021 08:48
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:2.0.1Release Notes
ucv-ext-asoc:1.0.24.tar
Uploaded: 02-Jul-2021 07:22
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:1.0.24Release Notes
ucv-ext-asoc:1.0.23.tar
Uploaded: 03-May-2021 13:40
Pull Command
docker pull hclcr.io/accelerate/ucv-ext-asoc:1.0.23Release Notes
Summary
The HCL AppScan on Cloud (ASoC) plug-in allows for integration with the HCL Appscan on Cloud server. This plug-in uses the Appscan on Cloud REST interface to interact with the HCL Appscan on Cloud application. Data is gathered from the ASoC server and displayed as a graphical view in the HCL DevOps Velocity portfolio.
History
The following table describes the changes made in each plug-in version.
| Version | Description |
|---|---|
| 3.0.19 | The older versions of ASoC plug-in was not reporting critical issues. The issue is fixed. |
| 3.0.16 | Segregated Static scan and Dynamic scan data. |
| 3.0.12 |
|
| 3.0.11 | Fix for Changed API. |
| 3.0.9 | Reduced vulnerabilities. |
| 3.0.5 | Auto-generated user access key related changes. |
| 3.0.1 | Added policy support. |
| 2.0.1 |
Note: This is a breaking change as the end point changes from ‘POST’ to |
| 1.0.24 | Proxy support added. |
| 1.0.23 | Removed IBM related keywords. |
| 1.0.18 | Bug fixes. |
Usage
To use the HCL AppScan on Cloud plug-in (ASoC), the plug-in must be loaded, and an instance is created before you can configure the plug-in integration. You can define configuration properties either in the user interface or in a JSON file of a value stream.
Integration type
The ASoC plug-in supports endpoint integration and a scheduled event integration.
Endpoint integration
You can use the ASoC plug-in’s endpoint integration to sync or import the scan data into HCL DevOps Velocity’s application vulnerabilities metrics by triggering the API endpoint with GET or POST request.
The endpoint integration is listed in the following table.
| Name | Path | Request Method |
|---|---|---|
| ASoC Scan | asocScan |
|
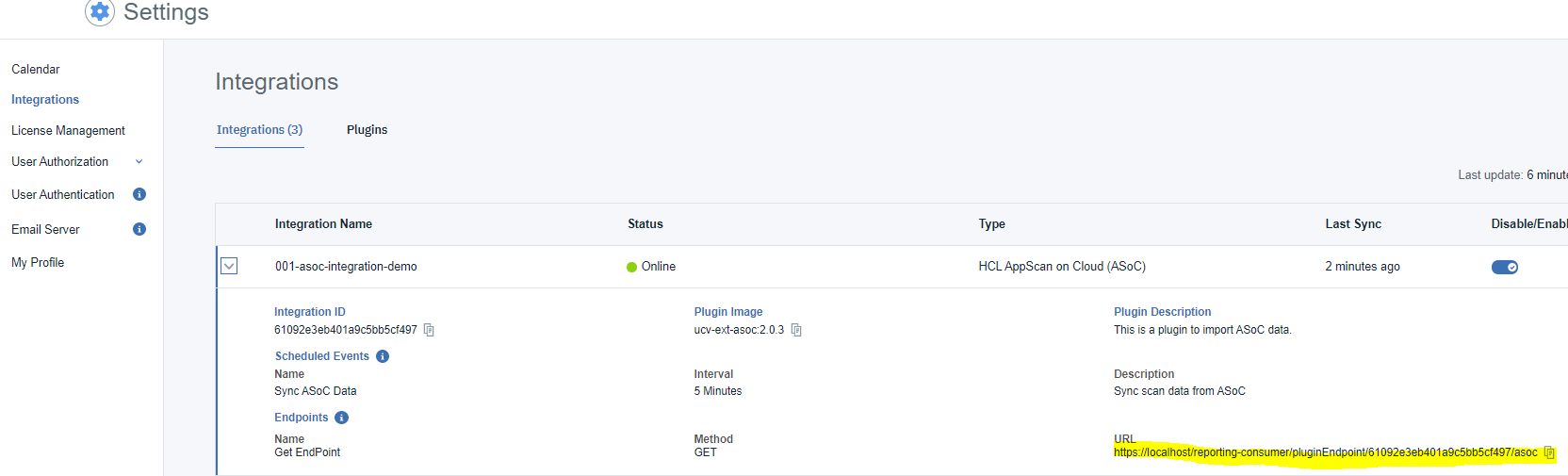
The following image shows the endpoint after the integration is defined in DevOps Velocity:
Notes
The following two features are available from version 2.0.1 or later of the plug-in:
- The plug-in imports historical scan data from ASoC.
- To sync or import the scan data into HCL DevOps Velocity, update the ASoC applications field in the plug-in configuration with the application names in ASoC. The plug-in will import the latest scan data from ASoC.
- The plug-in supports ASoC webhooks.
- The plug-in endpoint can be defined as a webhook in ASoC. When the webhook is called by ASoC after every scan execution, the plug-in will run and import the scan data from ASoC to HCL DevOps Velocity.
- To call out ASoC scan using REST API, pass the ‘build url’ as a ‘Comment’ as shown in the below example. As a result, the plug-in imports the ‘build url’ and associate the scan result to the specific ‘build’ / ‘build url’ in HCL DevOps Velocity.
curl --location --request POST 'https://cloud.appscan.com/api/v2/Scans/MobileAnalyzer' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Bearer bearer-token-goes-here' \
--data-urlencode 'ApplicationFileId=file-id-goes-here' \
--data-urlencode 'ScanName=scan-name-goes-here' \
--data-urlencode 'AppId=ASoC-AppId-goes-here' \
--data-urlencode 'Execute=true' \
--data-urlencode 'Comment=https://build-url-goes-here'- Running the ASoC scan using User Interface (UI) will not associate the scan result to the build url in HCL DevOps Velocity.
- To use the webhook, you must install AppScan presence on the machine where HCL DevOps Velocity is running. For more information, see ASoC documentation.
- The following is an example of creating a webhook in ASoC.
curl --location --request POST 'https://cloud.appscan.com/api/V2/Webhooks' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--header 'Authorization: Bearer bearer-token-value-goes-here' \
--data-urlencode 'PresenceId=presence-id-goes-here' \
--data-urlencode 'Uri=plugin-endpoint-goes-here?ScanExecutionId={SubjectId}' \
--data-urlencode 'Event=ScaneExecutionCompleted' \
--data-urlencode 'Global=true'
The following example shows calling the plug-in end point using a ‘non webhook’ method, such as CURL, Postman, or as a part of the CI/ CD pipeline.
Send an HTTP GET (For version 2.0.1 or later) or HTTP POST (For version 2.0.0 or earlier) request to your endpoint.
Sample endpoint:
https:///pluginEndpoint//asocScan
The payload for the POST is shown below.
{"scanId":"", "buildUrl": ""}.
| Name | Description | Required |
|---|---|---|
| scanId | The scan ID from the scan ran in ASoC. It is a mandatory field to render the scan results in Insights. | Yes |
| buildUrl | The build URL from the CI/CD tool such as Jenkins, HCL launch and so on. It is an optional field which links the ASoC scan results with HCL DevOps Velocity | No |
Scheduled integration
You can use the HCL AppScan on Cloud plug-in’s scheduled event integration to automatically sync or import the scan data into HCL DevOps Velocity’s application vulnerabilities metrics at regular interval of time. Currently, HCL AppScan on Cloud plug-in sync or import scan data from HCL AppScan on Cloud to HCL DevOps Velocity at an interval of 5 minutes.
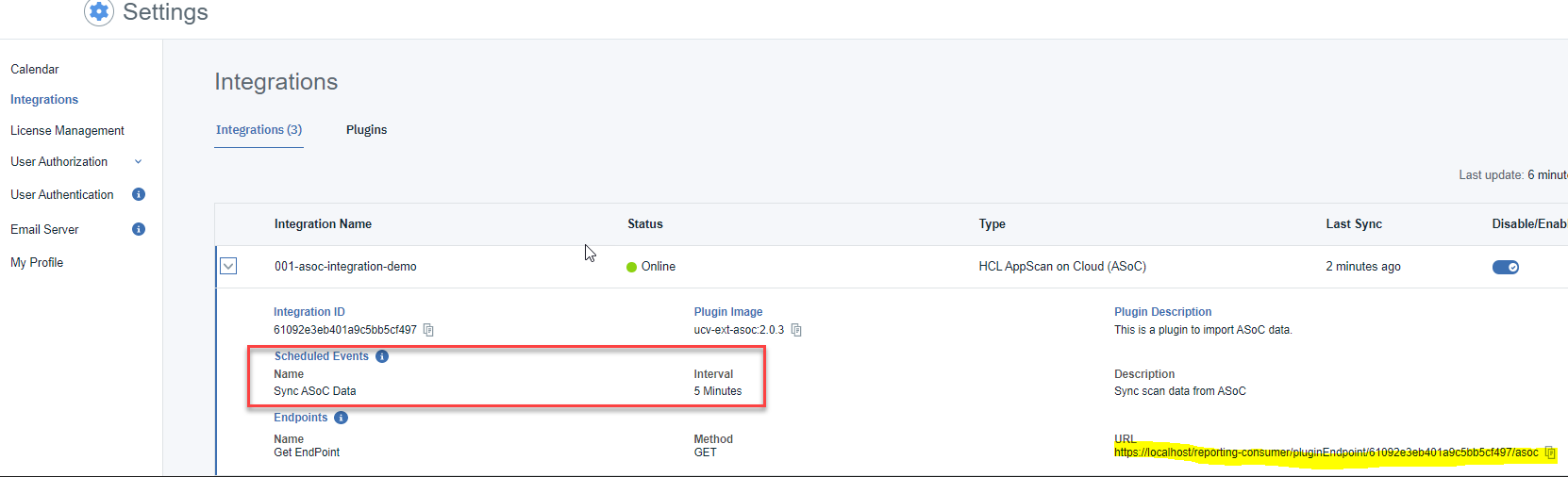
The following image shows the Scheduled Event after the integration is defined in HCL DevOps Velocity:
Integration
There are two methods to integrate the plug-in:
- Using the user interface
- Using a JSON file
The tables in the Configuration properties topic describe the properties used to define the integration.
Using the user interface
To install the plug-in, perform the following steps:
- From the home page, click Settings > Integrations > Available.
- In the Action column for the ASOC plug-in, click Install.
To integrate the plug-in, perform the following steps:
- From the home page, click Settings > Integrations > Installed.
- In the Action column for the ASOC plug-in, click Add Integration.
- On the Add Integration page enter values for the fields used to configure the integration and define communication.
- Select the Run as Scheduled Event checkbox.
Note: Select the checkbox only if you want to integrate the plug-in as a scheduled event and clear the checkbox if you want to integrate the plug-in as an endpoint. - Click Save.
Using a JSON file
The JSON file contains the information for creating a value stream. Within the JSON file there is a section for integrations. In this section the plug-in properties can be defined.
- From a value stream page, download the value stream map. The value stream map is a JSON file used to define integrations.
- Edit the JSON file to include the plug-in configuration properties.
- Save and upload the JSON file. This replaces the current JSON file with the new content.
- View the new integration on the Integrations page.
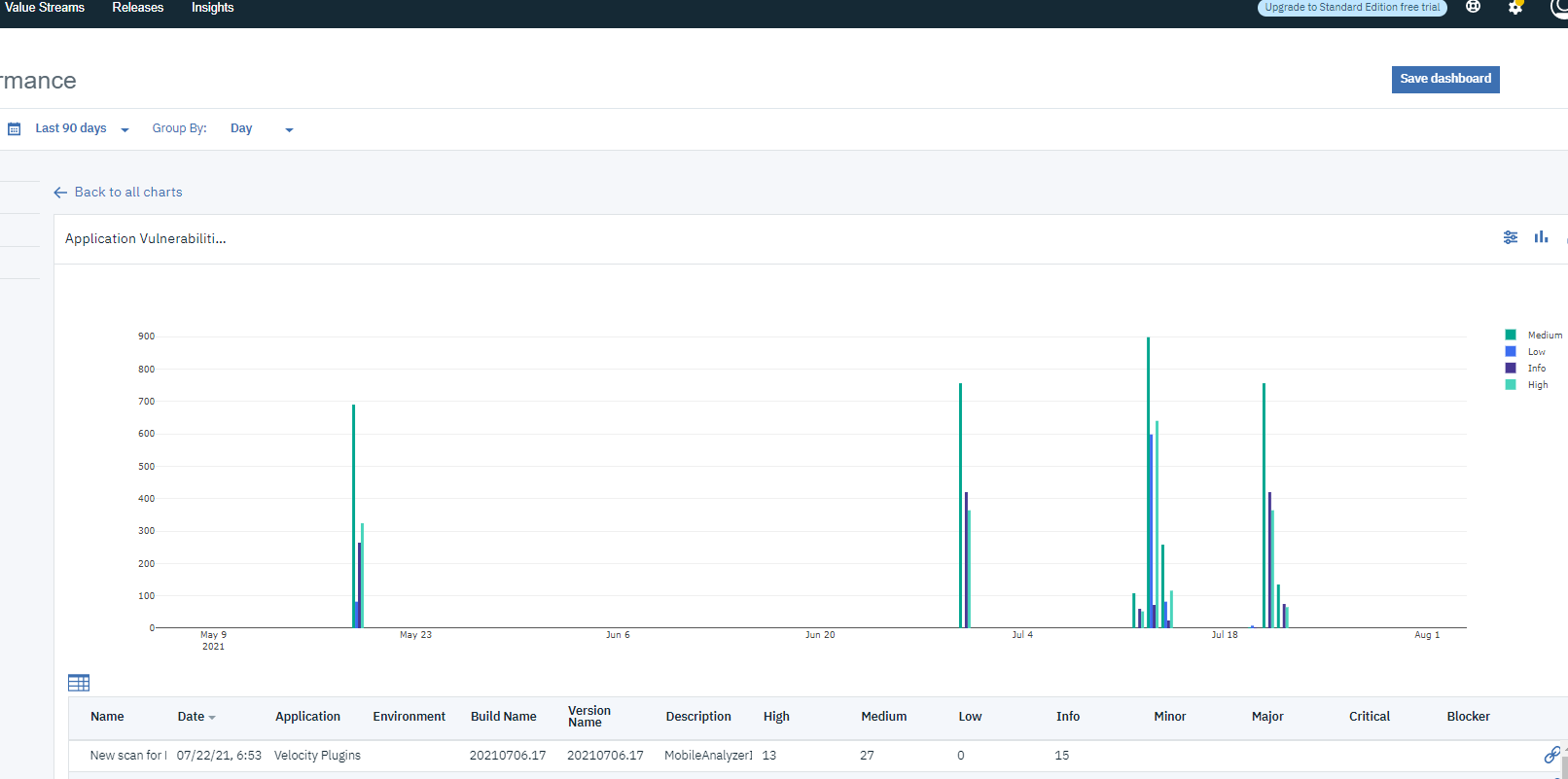
The following image shows the ASoC scan results in the Insights section of DevOps Velocity after the successful plug-in integration.
Minimum permission to integrate with HCL AppScan on Cloud (ASoC)
The HCL AppScan on Cloud (ASoC) Account used to generate the token must have access to the project which is being integrated with HCL DevOps Velocity.
Configuration Properties
The following tables describe the properties used to configure the integration. Each table contains the field name when using the user interface and the property name when using a JSON file.
- The General configuration properties table describes configuration properties used by all plug-in integrations.
- The HCL AppScan on Cloud configuration Properties table describes the configuration properties that define the connection and communications with the HCL DevOps Velocity server. When using the JSON method to integrate the plug-in these properties are coded within the
propertiesconfiguration property.
Some properties might not be displayed in the user interface, to see all properties enable the Show Hidden Properties field.
| Name | Description | Required | Property Name |
|---|---|---|---|
| NA | The version of the plug-in that you want to use. To view available versions, click the Version History tab. If a value is not specified, the version named latest is used. | No | image |
| Integration Name | An assigned name to the value stream. | Yes | name |
| Logging Level | The level of Log4j messages to display in the log file. Valid values are: all, debug, info, warn, error, fatal, off, and trace. | No | loggingLevel |
| NA | List of plug-in configuration properties used to connect and communicate with the HCL AppScan on Cloud Configuration server. Enclose the properties within braces. | Yes | properties |
| The name of the tenant. | Yes | tenant_id | |
| NA | Unique identifier assigned to the plug-in. The value for the HCL AppScan on Cloud Configuration plug-in is ucv-ext-asoc |
Yes | type |
| Name | Type | Description | Required | Property Name |
|---|---|---|---|---|
| Key ID | String | The key ID to authenticate with the Application Security On Cloud server. | Yes | keyId |
| URL | String | The URL of the Application Security on Cloud server. | Yes | asocUrl |
| Key Secret | Secure | The key secret to authenticate with the Application Security On Cloud server. | Yes | keySecret |
| HCL DevOps Velocity Access Key | Secure | The user access key to authenticate with the HCL DevOps Velocity server. | Yes | ucvAccessKey |
| ASoC Applications | Array | Comma separated list of Application names in ASoC – eg: App1, App2. | No | applications |
| Run as a Scheduled Event | Boolean | To integrate the plug-in as a Scheduled Event. Set this property to “true” to run the integration as a scheduled event. | No | isScheduledEvent |
| ASoC Policies | Array | Comma separated list of Policy names in ASoC – eg: OWASP Top 10 Mobile 2016, International Standard – ISO 27002 | No | ASoC Policies |
| Workflow Id | String | The value stream that this metric is associated. | No | workflowId |
| Proxy Server | String | The URL of the proxy server including the port number | No | proxyServer |
| Proxy Username | String | The user name used to authenticate with the proxy server | No | proxyUsername |
| Proxy Password | Secure | The password used to authenticate with the proxy server | No | proxyPassword |
JSON code sample
The following sample code can be used as a template to define the integration within the JSON file for a value stream. Copy and paste the template into the JSON file Integration section and make the appropriate changes.
"integrations": [
{
"type": "asocPlugin",
"tenant_id": "",
"name": "",
"properties":{
"ucvAccessKey": "",
"keyId" : "",
"keySecret":"",
"isScheduledEvent":"false"
"asocUrl":"",
"applications":""
}
}
]


 Configuration Properties
Configuration Properties

